Authentication
Get started
Security lies at our heart, so we have taken steps to help you to process transactions more safely. To reduce the risk that someone other than you can use your integration, our platform uses security codes linked to your PSPID.
The so-called API Key and API Secret provide a unique signature to the traffic between your system and our platform. You can define these for each of your PSPIDs in the Merchant Portal. Any server-to-server request from your system to our platform (via your PSPID) needs to contain both the API Key and API Secret. Our platform tries to match the codes we receive from you with the ones configured in the Merchant Portal.
Our Server SDKs offer a simple solution for this mechanism, requiring only few lines of coding. If you wish to use your own software, manual implementation is also possible.
Target most up-to-date API base URL
We encourage you to always target the most up-to-date API base URL when sending requests to our platform. Have a look at our dedicated guide for a full overview.
To allow you a smooth transition, previous API base URLs remain available until further notice.
2. Configure API key and API secret
To configure the API Key and API Secret in your PSPID, follow these steps:
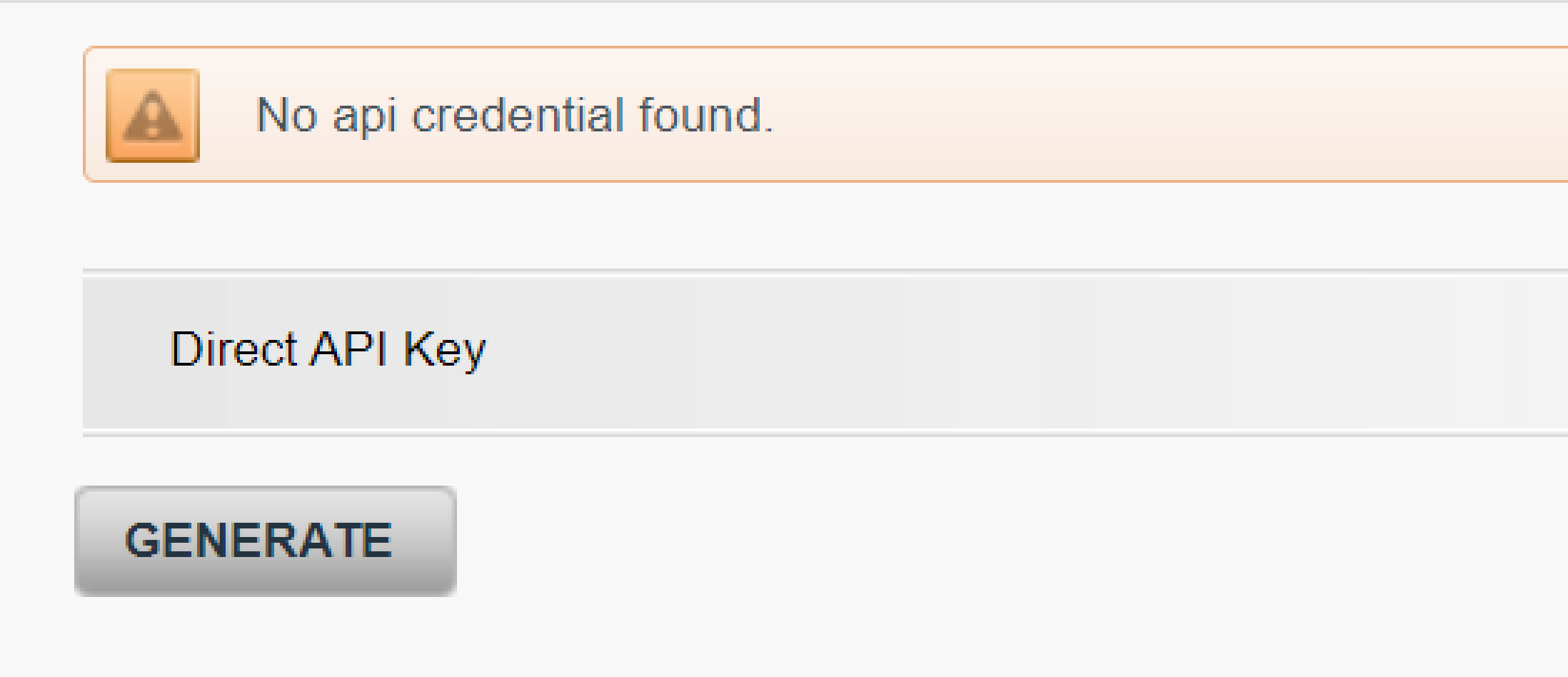
- Login to the Back Office. Go to Configuration > Technical information > API settings > Direct API Key
- If you have not configured anything yet, the screen shows “No api credential found”. To create both API Key and API Secret click on “GENERATE”
- The screen now shows both codes in the table in the “Key” / “Secret” column respectively
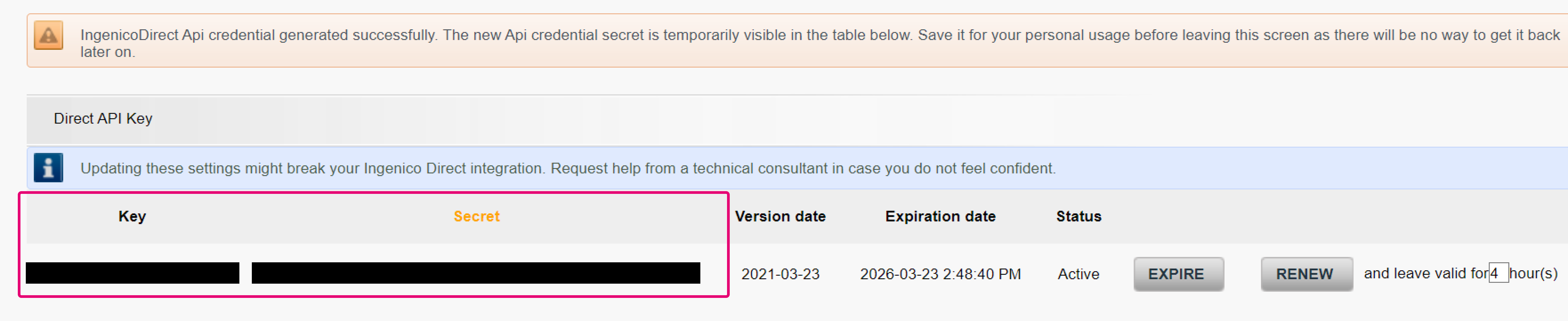
| Key | The current key configured in this PSPID |
| Version date | The date when the Key/Secret pair was created |
| Expiration date | The date when the Key/Secret pair will expire. Default time of permanency is two years |
| Status | The current status of the API key/secret pair
|
If you wish to use a new API Key and API Secret, follow these steps
- Select a period from the drop down menu “leave valid for X hour(s)”. Click on the “RENEW” button. The currently used API Key/Secret pair will expire after the date as defined in “Expiration date”
- At the same time, a new API Key/Secret appears in the first line of the table. Make sure to save the API Secret in your system, as it will not be visible in the Back Office anymore once you access this menu anew
- To force an immediate expiration of the expiring API Key/Secret, click on “EXPIRE”. Our platform removes the respective API Key/Secret from the table and our platform, making it unusable for requests
Use API key and API secret with SDKs
Once you have set up your API Key/Secret in the Merchant Portal, you can use them for requests you send to our platform. Our Server SDKs make it really easy to do so.
Have a look at this code sample that demonstrates how to add them in a standard Hosted Checkout Page request:
Authenticate without SDKs
You can use our API without the SDKs by sending requests to our endpoints directly. This requires you to follow a different authentication mechanism.
Essentially, you need
- To hash with your API Secret over several HTTP headers (the signature contents or signed-data) you send along with your request
- Send this hash (the signature) together with your API Key to verify the authentication
Have a look at the following chapters to understand how this works and our GET, POST and DELETE examples.
Understand authentication process
A GET/POST/DELETE request following this approach includes the following steps:
- Create a string-to-hash, consisting of several HTTP headers
- Calculate the hash using the algorithm HMAC-SHA256 with your API Secret
- Send the actual request to our platform, including the headers, the hash and your API Key
1. Create string-to-hash
Compose the string-to-hash (the signature contents or signed-data) by following these rules:
Order of the headers
The string-to-hash consists of the following headers, listed in a specific order:
<HTTP method>
<Content-Type>
<Date>
<CanonicalizedHeaders>
<CanonicalizedResource>
Header Content Conventions
Each header is constructed as follows:
<lowercased header name>:<header value>;
Apply the following conventions for the content of the headers:
| Headers | Conventions |
|---|---|
| <HTTP method> | Use either "GET," "POST," or "DELETE" (always in uppercase) depending on the HTTP method used. |
| <Content-Type> | Use the fixed value "application/json; charset=utf-8" for POST requests and use an empty string for GET or DELETE requests. |
| <Date> | Use the "Date" header in RFC1123 format. |
| <CanonicalizedHeaders> | Include custom headers specific to your application, such as X-GCS-ClientMetaInfo. |
| <CanonicalizedResource> | Include the target URI without the HTTP method, and include all decoded query parameters. |
Unwrap Header Values
If a header value is wrapped over multiple lines, unwrap each line as described here. Unwrap by replacing a new line or multiple spaces by a single white space.
Have a look at this example:
A very long line<CR><LF>
<SPACE><SPACE><SPACE><SPACE>that does not fit on a single line
becomes
A very long line that does not fit on a single line
Trim White Spaces
Trim all whitespaces which exist at the start and end of the value.
Have a look at this example:
<space><space><space>Some text<space><space><space>
becomes
Some text
Ensure that each <item> is followed by a new line (line feed), including the last item.
Have a look at this code sample for a CreateHostedCheckout request:
Have a look at the GET example or the DELETE example in our dedicated chapter to know exactly what you need to do
2. Calculate hash
Once you have created the string-to-hash (the signature contents or signed-data), you need to hash it via the MAC algorithm HMAC-SHA256 with your API Secret.
The result of the hashing is the signature you need to provide in the authorisation header of your request.
Have a look at this code sample:
3. Send request
Finally, you can send your request, including
- The headers you used for creating the string-to-hash (the signature contents or signed-data)
- The base64-encoded hash result (the “signature”) and your API Key (which our platform uses to identify your PSPID on our account) in the HTTP header 'Authorization' according to this formula:
Authorization = "GCS v1HMAC:" + API Key + ":" + signature - The JSON-encoded request body for POST requests (GET/DELETE do not require a request body)
Have a look at this code sample:
Understand string-to-hash examples
As the general requirements for a GET/POST/DELETE request differ, the construction of the string-to-hash does as well.
Have a look at the following examples to learn how to implement them in your system:
1. POST request
The string-to-hash (the signature contents or signed-data) for a CreateHostedCheckout request:
POST
application/json; charset=utf-8
Wed, 02 Mar 2022 11:15:51 GMT
/v2/yourPSPID/hostedcheckouts
2. GET request
The string-to-hash (the signature contents or signed-data) for a GetHostedCheckout request:
GET
Wed, 02 Mar 2022 11:15:51 GMT
/v2/yourPSPID/hostedcheckouts/yourHostedCheckoutID
- There is an empty string for Content-Type header, as GET request do not have a request body
- There is a new line (line feed) after the last header (URI resource)
which you also need to consider when hashing the string
3. DELETE request
The string-to-hash (the signature contents or signed-data) for a DeleteToken request:
DELETE
Wed, 02 Mar 2022 11:15:51 GMT
/v2/yourPSPID/tokens/yourTokenID
- There is an empty string for Content-Type header, as DELETE request do not have a request body
- There is a new line (line feed) after the last header (URI resource)
which you also need to consider when hashing the string